
Tandemworld eNewsletter for March 2016
Platinum Sponsor is
Gold Sponsor
Silver Sponsor
Tandemworld eNewsletter
for March 2016
Contents
Tributary
Systems’ Storage Director 5.0 for NonStop Professionals
**NEWS FLASH**
XYPRO - Detecting “the Low and Slow
(attack)” with XYGATE SecurityOne™ NEW LOOK
BITUG NEWS
Musings on NonStop! - March, ‘16
DataExpress
The OmniPayments 50%-Less Guarantee: How Do We Do That?
XYPRO - HPE SecureData and XYGATE Data Protection™ (XDP), a powerful combination
comForte - Demystifying Tokenization: Payment Versus Security Tokens
Gravic Publishes New HPE Shadowbase Case Study on BASE24™ Business Continuity
CSP - New NonStop PCI Compliance and File Integrity Monitoring
Integrated Research
3 REASONS TO CONSIDER LUSIS LITEPOS FOR 2016
Meet comForte at the European NonStop HotSpot event in Berlin
TANGO: THE "DO SOMETHING" OPTION TO LEGACY PAYMENT SYSTEMS
Spring Events Summary NuWave
The Availability Digest Reviews the HPE Cyber Risk Report 2016
comForte at events near you in 2016
XYPRO looks forward to seeing you throughout 2016
Current Subscribers 15102
Tributary Systems’ Storage Director 5.0 for NonStop Professionals
By Glenn Garrahan, Director of HP Business for Tributary Systems
“NonStop professionals know Tributary Systems!”
That might seem to be a bit over-reaching, but really it isn’t. Tributary Systems has been the OEM supplier of all versions of NonStop Tape for over 18 years. Whether it was Tandem, Compaq, HP or now HPE, TSI has been there for the NonStop professional.
But not just tape drives alone. All the NonStop Media Manager software products for Oracle library connectivity and functionality were developed and productized by TSI.
These Tributary Systems products have been and continue to be some of the most robust and reliable OEM products NonStop has offered. TSI understands how important this is to NonStop professionals, and we continue to support our current OEM products for our partners at HPE.
Storage Director 5.0 builds on our long and successful history of supplying innovative excellence to our NonStop professional customers!

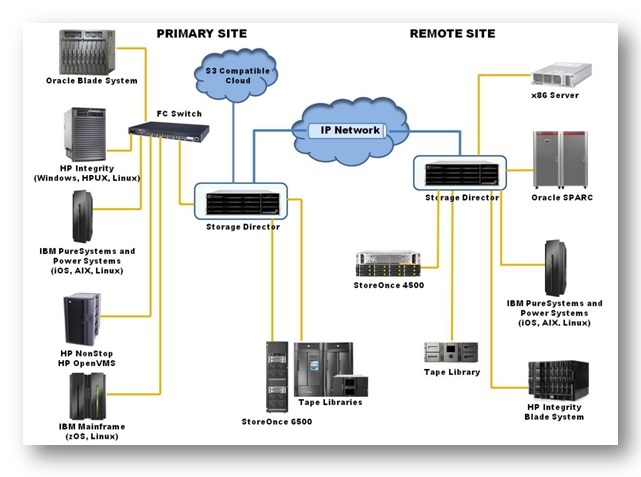
Tributary Systems’ Storage Director® V5.0 is a backup storage virtualization and consolidation solution. Storage Director is an any host platform to any storage media or device solution that virtualizes and consolidates backup storage in any heterogeneous datacenter. Storage Director was designed for fault-tolerant, high availability computing environments and meets or exceeds most data backup requirements for speed, capacity, compatibility, and reliability.
●
Provides fully automated backup, restore and DR operations●
FlashSystem can be added to provide industry leading data read/write performance to support applications needing the fastest possible access to data●
Scales seamlessly by adding nodes to meet performance requirements and add cache for multiple petabytes of storage●
Data-at-rest LZ compression/AES256 encryption is available on both disk cache, flash cache, NAS, physical tape media and replication●
Transparent remote backup-and-restore features to satisfy off-site archival requirements●
Enables alternate site disaster recovery schemes●
User-defined policies allow flexible tape, disk, flash, cloud and data migration strategies●
Supports heterogeneous, multi-platform environments on a single Storage Director system●
Customized configurations for higher availability and specific customer needs●
Supports tape library distribution and consolidation●
Provides Flash and LTO library support for zOS and zLinux Mainframes●
FICON connectivity for zOS Mainframe applications●
Enables NonStop data migration to S3 compatible clouds●
Enhanced data security provided by OS appliance configuration
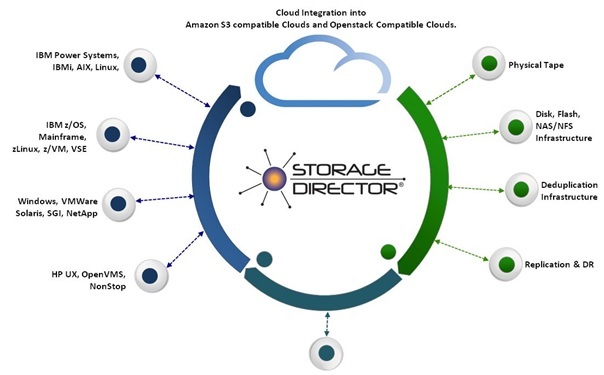
All Backup Application Support:Veritas NetBackup, CommVault Simpana, Tivoli Storage Manager, Veritas Backup Exec, CA ARCserve, Veeam, HP Data Protector, etc.
Sto
rage Director offers any-to-any compatibility with infinite scalability and industry leading performanceStorage Director offers a state-of-the-art backup storage consolidation platform which can handle requirements from even the most complex environments. Storage Director implements a wide variety of data protection schemes and tape library consolidation, thus eliminating the need to dedicate devices for specific backup purposes.
Fully Automated Backup and Restore Operations
The technology within Storage Director brings a scalable, flexible, and high-throughput solution to backup and restore operations. No longer does operations staff need to monitor data movement. Storage Director provides dynamic drive sharing; customer defined virtual tape policies, backup to local and remote sites, and a performance improvement over current backup methods.
Multi-Platform Heterogeneous Environments
Storage Director emulates several standard front-end interfaces in which existing backup servers and applications can connect and control. Because Storage Director adheres to using standard interfaces, backup servers can reside on nearly any platform and operating system in the market today. This includes all open platforms (x86 Intel® or AMD based systems) as well as IBM iSeries™ (AS400), IBM Power Systems™ (running AIX, Linux®, and i/OS), HP OpenVMS, HP UX, Sun® SPARC, and blade systems (running Windows, Linux and UNIX®). Storage Director also has custom developed interfaces for proprietary computing platforms such as IBM Mainframe (running z/OS™ and zLinux) and HPE NonStop (Tandem).
Customized Configurations
Storage Director is available in the following configurations: ANTARES 1500, ANTARES 2500, ANTARES 3500 and ECLIPSE. ANTARES is a low cost, self-contained 3U backup storage appliance for all IBM, HP, Oracle/Sun and open computing platforms running Windows, Linux and UNIX operating systems. ANTARES is also compatible with NetBackup, Simpana, TSM and other backup applications. ECLIPSE is a zero cache solution designed as a translation/ compatibility platform fronting existing backup and de-duplication solutions.
Backup sizes, throughput requirements, tape retention policies, availability requirements, as well as future growth rates will determine which model best fits a customer’s needs.
Scalable and Expandable
As backup requirements change, so too can Storage Director. Additional virtual libraries, drives, and tapes are easily added through a web-based GUI. Additional disk cache enclosures can be introduced into the system and throughput performance and higher availability can be achieved through the multi-node architecture. Storage Director will meet the needs of today and protect your investment by meeting a different set of needs tomorrow.
Contact Information
or visit our website: www.tributary.comTributary Systems, Inc. is a technology solution provider to enterprise computing customers. Tributary develops and sells data protection, backup storage, virtualization, site-to-site replication and disaster recovery solutions. Tributary is an acknowledged global leader in providing backup storage and data protection solutions for fault-tolerant, high availability, enterprise computing environments.
Tributary was founded in 1990 and is a Texas based company with its headquarters, development, integration, and test facilities in Bedford, Texas.
Through its channels and direct sales organization, Tributary has served customers worldwide, predominantly in the banking, financial services, retail, telecom and healthcare industries. Tributary is a HPE business partner and OEM supplier, IBM OEM Partner (iOEM), Solution Reseller (ISR) and Business Partner, Quantum® Value-Added Reseller (VAR), and Oracle® OEM partner.
**NEWS FLASH**
This month’s discussion topic follows but first I wanted to share some important news.
Two of our Customers have now migrated to production on the Xbox with ZERO downtime using the features of DRNet. This is a first in our industry.
===============================================================
Opening up the Tandem
Back in 2000 when I was CTO of Insession Technologies I had a number of discussions with my friends at ACI about migrating Base24 data to open platforms to simplify customer reporting. While it made sense to enable customers to build their own reports and ad hoc queries, there was simply too much investment in custom built SCobol reports to win the argument.
Well, that argument has continued for all these years and now we are seeing a shift. Base24 customers are migrating real-time transactional data to open platforms for reporting. Rather than building new reports on the Tandem, or investing in more RPQ’s to modify transaction formats, they are replicating real-time transactional data to open relational databases and using industry standard reporting tools. This trend is not limited to our Base24 base. Some of our Connex customers are heading in the same direction.
Syncing Tandem data real-time to an external relational database is not a simple task. The trick is figuring out how to export your Unaudited Enscribe TLF or PTLF into a relational format. Speed and reliability are critical.
About 7 years ago our engineers solved this problem. We used the infrastructure of our proven Tandem-to-Tandem replication architecture. We used XML (Extensible Markup Language) to describe the Tandem data, and we used XSLT (Extensible Stylesheet Language Transformations) to transform and load the data into the open databases. Simple. Clean. Flexible. Portable. Standard. Works across most open platforms.
Our Engineers also designed DRNet/OPEN so that it can be installed as a component of a more comprehensive DR strategy, or installed stand-alone as a companion product to RDF.
Cool stuff, but for many years we had relatively few customers doing much with DRNet/OPEN. We had lots of industry interest but very few specific projects to implement. That seems to have changed in the last 6 months. While I would like to tell you all about what a deep thinker I am, and about how I can see the future of the Tandem, the latest trend caught me by surprise. Demand for DRNet/OPEN has jumped. First one customer, then another, then 4 more, and now two more. All wanting to figure out how to sync Base24 or Connex data with open platforms. Some are going to Oracle. Some to SQL Server. The flow of data is from the Tandem to OPEN but not OPEN back to Tandem.
We have been replicating Tandem-2-Tandem….for about the past 30+ years.
We have been replicating Tandem-2-OPEN… for about the past 7 years.
We have been replicating Tandem-2-CLOUD…. For about the past year.
DRNet® is world class NonStop Data Replication technology.
· Real-time Active/Active Data Replication
· Real-time Tandem to OPEN Data Replication
· Real-time File Synchronization
· Refreshingly Real-Time Support from Real Engineers
Jim.McFadden@network-tech.com
+1 (402) 968 3674
XYPRO - Detecting “the Low and Slow (attack)” with XYGATE SecurityOne™

Security has been a lifelong passion of mine. Growing up, I constantly pushed the envelope of what was possible. This was strictly for “research” purposes of course. I would spend a lot of my time after school (and sometimes during school) seeing what systems I could gain access to, discovering obscure security “features”, using social engineering or exploiting just plain security negligence . This was for no other reason than self-satisfaction, to cure a little bit of boredom and, to obtain some online fame. It was fun. I felt cool. I WAS that kid in my parent’s basement, but as I was sitting in my parent’s basement banging away on my keyboard, I was pwning your tech! The dot-com bubble was just forming and n00bz didn’t stand a chance.
I look back at the wealth of experience gained from the need to alleviate boredom in my early life and wonder how trivial it would have been for someone to notice what I was doing and to shut me down, but in the late 90s, security wasn’t just an afterthought – it was virtually non-existent. No one was keeping an eye out whether the system was being used for anything other than for what it was originally intended.
MTTD in Today’s World
Fast forward twenty years and security is at the forefront of everyone’s minds, yet common security oversights of best practices and negligence are still very much part of today’s landscape. The Mean Time To Detection (MTTD) of a security incident is still close to 200 days. That translates to an attacker residing in your systems for nearly six months on average until someone notices, that is – if – someone notices. In my day, the issue was that no-one was tracking my activities – nowadays there is audit data being generated everywhere. The problem has shifted from not enough data to too much data.
Figure 1.¹
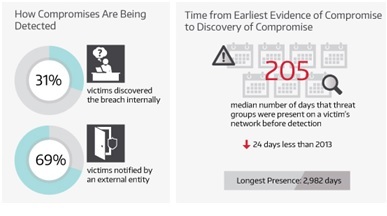
In an era where everyone is used to, and in fact demands, instant gratification, and where we have a one hundred billion dollar plus cyber security industry providing the tools and solutions to satisfy that demand, MTTD is still nearly 6 months! We cannot underestimate the ability of criminals to stay ahead of conventional solutions by constantly adapting – allowing them to hide their malicious intentions or simply fly under the radar. These low and slow attacks have become the Achilles heel of organizations worldwide. The data breaches that will be announced next year are taking place right now, as you’re reading this article. The attackers are already in the networks and systems doing their reconnaissance work, exfiltrating data, planning their next move – for months and years at a time, blending into the noise of everyday business users and operations. How can one detect these anomalies?
Data is King

We use data every day to gain insight, plan our next moves and run our organizations. Too little data and you’re not getting the complete picture to make an informed decision. Too much data and you’re overwhelming your staff and drowning in the noise to make any sense out of it all. Analyzing the vast amounts of data to detect pattern anomalies requires specialized knowledge and takes time. Attackers know this.
Traditional SIEMs and log management devices do what they do well. They aggregate data from multiple sources, report on the verticals you tell them to report on, and allow your auditor to put a tick in the PCI-DSS compliance checkbox for requirement 10.5.3. You would think that should make your CISO sleep better at night, but ticking the compliance box is all that exercise will allow you to do.
We are bombarded by marketing buzz words like “Big Data” and “Data Lakes”; how can we strip away the marketing buzz in order to introduce the concepts into our security strategy and use them to our advantage?
Hello Security Intelligence!
Security Intelligence and Analytics is the concept of collecting, normalizing and correlating the data that you already have access to from myriad systems and solutions that have been deployed in the enterprise.
This minimizes the reliance on the human element in what is typically a time consuming exercise for highly skilled data scientists. Applying computer based algorithms and data analytics to the vast amount of data in order to detect valid security events introduces a new dimension to data intelligence that can be used for tracking security incidents before they occur, ultimately reducing the Mean Time to Detection. Potentially saving organizations millions of dollars and often more importantly – from appearing on the front pages.
Security Intelligence algorithms and analysis techniques take the data sets that are already being generated from disparate sources in your enterprise, such as security audits, application logs, network flows, vulnerability management, configuration data, keystroke logs etc… It slices and dices that data, pivots the data and ultimately correlates the common elements between these unrelated sources while adding a layer of context to the correlation based on specific indicators of compromise for that system. You have now armed yourself with a proactive method to track anomalies and detect security events important to your environment, while separating the noise from the actionable data.
This real time correlation and contextualization of data sources enables notifications to security analysts of the anomalies that are being measured on a system as they’re occurring. Say for example commands are being issued on a system that are not typical of the user issuing them. By recognizing this and correlating that activity with suspicious network flow and additional sources of data, security intelligence algorithms can detect and alert that something is happening on the system that is outside of what is normal for the given environment. This powerful concept provides meaningful interpretation of the data, allowing security practitioners to have the upper hand in detecting suspicious activity before you’ve reached the tipping point.
XYGATE SecurityOne™ – Security Intelligence and Analytics for the NonStop
Mission critical systems like the HPE Integrity NonStop Servers house an organization’s most valuable applications and assets and must be protected against a variety of threats. Although the NonStop has unique security features not typically seen on other enterprise systems, it is still at risk from insider and outsider threats, misuse, non-compliance and security breaches. As systems grow larger, faster and more economical, the amount of data generated, and thus put at risk, exponentially increases. Keeping track of what is happening to that data and those systems becomes a very expensive and inefficient exercise for system operators. Without proactive control and visibility into their NonStop infrastructure, organizations expose themselves to greater risk. Current solutions do not provide the specialized NonStop security intelligence and contextualization to paint the correct picture for this purpose.
XYPRO is proud to announce XYGATE SecurityOneTM . A brand new product that provides a comprehensive, single pane of glass approach to control and contextualize NonStop security through policy management, data protection and security analytics. The result? Meaningful reduction in the Mean Time to Detection.
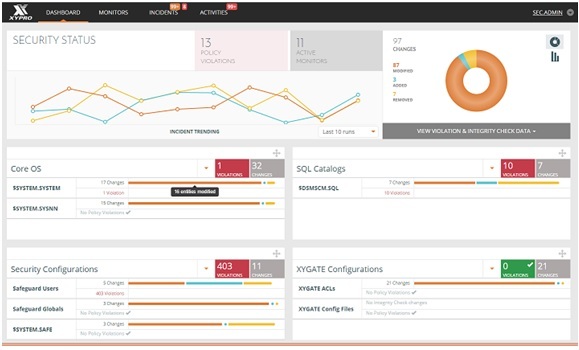
XYGATE SecurityOneTM introduces an intelligence platform never seen before for the HPE Integrity NonStop Server. Leveraging existing native HPE NonStop security information, all of the XYGATE suite’s extensive security data information and extensive new functionality, XYGATE SecurityOne™ incorporates multiple NonStop security intelligence data feeds into a single, easy to use, browser interface for a single-view visibility of your NonStop Systems’ security.
Using our patent pending technology, XYGATE SecurityOneTM gathers data from multiple, disparate NonStop server sources and uses specialized security intelligence algorithms to correlate, contextualize and analyze events. For example, combining application data, user behavior, file operations, network data, command input and other sources to paint a detailed security incident picture in real time for the NonStop, enabling security operators to hone in on and detect security events before they culminate into an “incident”. XYGATE SecurityOneTM draws your attention and alerts you to the items you need to be aware of, allowing you to effectively prioritize your response and countermeasures.
With its summary/detail dashboards and customizable, easy to use browser interface, XYGATE SecurityOneTM enables you to manage security configurations, harden your system security based on NonStop best practices, measure and enforce compliance and policies on a global level, take the guess work out of audit and forensic investigations, intelligently analyze your NonStop security data and much more.
The value of security intelligence and the way it takes the human effort involved in data analysis, contextualization, correlation and pattern matching and automates it cannot be underestimated. This complex analysis allows for efficient and effective processing of security data so your security team can make quicker, informed decisions on events that are relevant to them. This in turn yields additional benefits by reducing operational costs, simplifies management, enhances security and increases response times. This is why Security Intelligence and Analytics have one of the highest perceived ROIs compared to its cost.
Organizations recognize the value of intelligence based on data analysis in other parts of their business strategy, like marketing – security intelligence is no different. Being able to leverage the data you already have access to through automated analysis empowers your organization to quickly and efficiently deal with the threats that are constantly evolving.
¹ Source: MANDIANT M-Trends 2015: A VIEW FROM THE FRONT LINES
Steve Tcherchian
CISO and Product Manager,
XYGATE
SecurityOne™
New Look
BrightStrand International Ltd would like to announce the Launch of their New Logo with the updated Website to follow shortly.

Our New website will be available soon detailing all the Services we offer NonStop Users across the EMEA region. Bookmark us at
www.brightstrand.com.
We hope to see you at GTUG on 18th – 20th Apr 2016 and the BITUG Big Sig on 11th/12th May 2016.


BITUG NEWS
BIG SIG: Thursday 12th MAY 2016
Venue: Trinity House, London. Website.
Date: 12th May 2016
BIG SIG Registration is now open: CLICK HERE TO REGISTER
Agenda: Visit http://www.bitug.com/big-sig/
BITUG Education Day: Wednesday 11th MAY 2016
Venue: HPE Offices, 1 Alderman Square, London EC2V 7HR.
Date: 11th May 2016
Education Day Registration is now open: CLICK HERE TO REGISTER
Agenda: Visit http://www.bitug.com/big-sig/
There will also be a BITUG networking evening on Wednesday11th May from 17:00 (Location TBA – visit http://www.bitug.com/big-sig/ for updates), all BITUG members are welcome.
Any enquires about these events please Email kpoultney@brightstrand.com
Kevin Poultney
Chairman, BITUG.
BrightStrand International Limited
Musings on NonStop!
March, ‘16
The
opinions expressed here are solely
those of the now self-employed author
There’s no question about it;
NonStop is on the move. After so many years of simply watching Tandem,
then Compaq and finally, HP, do just enough to retain the biggest users
of NonStop systems, the work done of late represents a huge step up in
both visibility of NonStop and HPE’s commitment to it. You really don’t
spend a quarter of a billion dollars and evidently, a lot more, on a
product that is hanging on precariously to its position in the product
portfolio. Not for the fainthearted are sums this big, and reading the
announcements that have followed it’s clear HPE has high hopes for the
future of NonStop.
If you think you have read this message from me before, let me tell you
the events of just the past couple of weeks have added to the storyline.
In prepping for a webinar sponsored by IR as part of their Payments:
House of Cards series, the move by NonStop into software, independent of
infrastructure, has accelerated. If you missed my presentation,
NonStop X – The New Goal, then click on the hyperlink or cut and
paste this link to replay the presentation in its entirety:
It was at the 2013 NonStop Technical Boot Camp where Randy Meyer made
public the work being done to port NonStop to the Intel x86
architecture. At the time, I took it squarely on the chin as I had
scoffed at such a possibility earlier in the year – at the request of
HPE, as at that time there was still a healthy backorder of NonStop I
systems to fulfil. Seems some of my earlier blog postings had hit a
little too close to home, but rolling out the new NonStop X family of
systems is exactly what HPE did. In the short video played to the
audience that featured Meg Whitman, CEO of HPE,
“Our NonStop customers truly make
it matter!”
If you missed reading about
this, check out the post of November 2013, to the NonStop community
blog, Real Time View:
The real deal - NonStop supports x86! And no, I haven’t quite looked
at a bottle of Cognac the same way ever since. The point though is that
this was just the beginning of the journey as not one but two members of
the NonStop X family of systems became available and if you had an
interest in a single core, dual core, even four and perhaps six cores,
HPE had a NonStop X model to meet your needs.
By the time the 2014 NonStop Technical Boot Camp was held we already
knew what the story line would be – the unveiling of the NonStop X NS7
X1. What we may not have fully appreciated was that NonStop development
was hard at work bringing forward the release date of the entry-level
system, the NonStop X NS3 X1. Just like that, what had been expected to
take many more quarters was about to be delivered ahead of schedule! Our
hats should be raised for the many hours of effort by NonStop product
management and development that went into making this all happen.
There was little time to lift off the gas, however. With the early 2015 GTUG event, HPE quietly informed us of Project Yuma and of the plans to use the new InfiniBand interconnect fabric to hook up NonStop X to other platforms and allow data to flow between these platforms and Nonstop systems at blistering speeds. What a coup – with HPE telling us all of their vision of the need to move into an idea economy. “Every company,” Whitman told audiences wherever she went, “is having to take their legacy IT systems and transform themselves so that IT can be a competitive advantage.”
Fair enough. We get it. Wire up NonStop and connect it to server farms, whether configured in support of clouds or not, and you can begin supporting the vision of an idea economy. Cool. But wait, there’s a whole lot more coming down the pipe – think Converged Infrastructure on steroids. Of course, by the time 2015 NonStop Technical Boot Camp came around, attendees got to hear it from Martin Fink, EVP and HPE CTO himself. “Now the question is ‘do we need a new strategy?’” Fink asked the NonStop community. “I don’t think we do. I think we need to take our software strategy to the mainstream. The mainstream software world today tends to revolve around 4 things: Linux, Virtualization Open Source and Cloud.”
It was a heady stuff, certainly,
and if you have a long history with NonStop then perhaps you are a
little uneasy at this stage. Infrastructure as code? A single API by
which we can quickly compose, decompose and then re-compose
disaggregated pools of compute, storage and a fast flexible fabric? HPE
Synergy? Even ContainerOS? All capable of accommodating NonStop at some
future point as NonStop development is working on the goal of making
NonStop free of all infrastructure – real, or otherwise. And then we
heard Fink admit that “In the labs, they have NonStop running in a VM on
Linux. It’s not ready to be a product, but it’s a proof point that we
can get there.”
Amazing! In the labs NonStop running in a VM on Linux! All of which is
by way of transition to the big news of this past month – it’s not
really in the labs anymore but being demonstrated in public. As first
reported in a discussion Can you Visualize NonStop in a Virtual World?
in the LinkedIn group, Real Time View, Check out the “Mobile World
Congress 2016 in Barcelona, Spain; will be interesting.” And why? Well,
under the heading of "Transfer to a hybrid infrastructure” HPE adds the
following. "Visit this demo to learn about the future of highly
available and massively scalable infrastructure for your core network.
This is a live demonstration featuring a potential HPE virtual NonStop
environment with x86 COTS (Commercial Off-The-Shelf) hardware. Touch and
see virtual network core functions of HPE I-HSS and INS." And what’s the
value for the NonStop community?
“Regarding the value
proposition, virtual NonStop would enable customers to fully utilize
their IaaS, run NonStop VMs and Linux VMs in the same physical server,
connected via YUMA (RDMA over RoCE / RDMA over Converged Ethernet).”
Said the NonStop development director most closely involved with the
project. “I see mention of just firing up another NonStop VM if a
physical server fails, rapidly bringing the virtual CPU back up. Also
think about the possibility of doing hot patches / SPRs by firing up a
second virtual NonStop system on the new SPRs running active/active,
then downing the ‘old’ virtual NonStop system.”
Yes, NonStop is on the move. As Fink continues to talk about the
mainstreaming of NonStop no one in the NonStop community should take
this lightly – HPE is making huge investments in NonStop and again, why?
Well problems with scale, fault tolerance, quality and even database are
best addressed with NonStop. There is nothing new about this, naturally,
as far as the NonStop community is concerned. However, what is new is
the attention NonStop is getting from HPE executives wherever they
present and with prominence comes acceptance. And this is big news for
all involved; NonStop is certainly on the move!
Richard Buckle
Founder and CEO
Pyalla Technologies, LLC
Email:
richard@pyalla-technologies.com
Following my blogs? My web publications? My discussion Groups?
Check out (or
copy and paste to your
browser):
Real Time View
at
http://www.itug-connection.blogspot.com/
…. And check out the Group on LinkedIn, Real Time View
comForte at http://blog.comforte.com/
…. And check out the Group on LinkedIn, comForte Lounge
ir.com Payments and Infrastructure at http://www.ir.com/blog-pay/
…. And check out the Group on LinkedIn, realtime.ir
WebAction.com at http://webaction.com/blog/
…. And check out the group on
LinkedIn, Data Driven Apps
ATMmarketplace at
http://www.atmmarketplace.com/blogger.php?id=130763
… And check out the Group on LinkedIn, ATM Industry Association
buckle-up at http://www.buckle-up-travel.blogspot.com/
…. And check out the SubGroup on LinkedIn, Pyalla Track Days
DataExpress
Can NonStop teach the rest of IT about best practices? Should NonStop
systems managers be involved with more than just the oversight of
NonStop systems under their care? When the boundary lines between
systems are becoming blurred and where a single business solution may
span multiple systems, should the NonStop team make their presence felt
more strongly?
It is easy for many within the NonStop community to look back at the
good old times when they were extremely proud of their systems –
capturing much of the front-end business of mainframes as they took on
more and more responsibility for running what was once called the online
systems. Fault tolerance actually meant something to these businesses
and the value proposition of running 24 X 7 was a distinct competitive
advantage.
Travelers returning from Japan would recount how ATMs across the country
would be unavailable for extended periods on select days of the week, to
the point where Japanese society simply accepted that it was de rigor
for computers not to be operational at some point. At least one of our
contractors recalls such experiences first hand. However, today, it
seems some of the value proposition we attribute to fault tolerance has
taken a back seat and yet, isn’t it time when we should be shining a
brighter spotlight on NonStop?
HPE continues to place emphasis on the transformation to a hybrid
infrastructure. This is executive talk for how best to accommodate the
legacy, or traditional, or contemporary data center that exists with the
introduction of cloud computing. No senior business executive is
prepared to simply throw out what’s already in place just for the sake
of it and budgets simply don’t accommodate dismantling working systems
on a whim. HPE is absolutely correct in its assessment that there is a
need for coexistence between what is in place with new technologies, and
in order to make such a mix of systems perform seamlessly a common
infrastructure, whether it’s external storage, a standardized middleware
option or even a single pane of glass for operators, needs to be
deployed.
At DataExpress we see great advantage in leveraging the emergence of
hybrid infrastructure for the benefit of our customers as well as
ourselves. Having now completed the testing of DataExpress NonStop (DXNS)
on NonStop X systems in cooperation with HPE NonStop and the Advanced
Technical Center (ATC), we are beginning to map out our plans to bring
to NonStop our DataExpress Open Platform (DXOP) product.
According to the HPE NonStop product roadmaps, 2016 is going to be the
year for Java 8.0 becoming a viable option on NonStop and this
represents a significant milestone for DataExpress. Not without teething
problems at some level, and understandably so, as each implementation of
a major Java release comes with a certain level of risk for any member
of the NonStop vendor community – but the upside is that greater number
of Java applications can be supported. And DXOP is one such candidate.
In combination with NonStop X and the significant uptick in performance
that comes with its support of the Intel x86 architecture, few members
of the NonStop community still harbor any doubts about either the
performance of Java on NonStop or about functionality. We all well
remember one high profile NonStop user having said recently how on
NonStop, “Java rocks!” But it’s not just the availability of Java on
NonStop per se, but rather, the completion of the NonStop journey to
becoming truly a part of mainstream computing.
Ultimately, many will have forgotten that there was a time when business
asked its IT organization whether an application could run on NonStop?
Had there been a successful port? How expensive would it be to bring it
over to NonStop? Today, with Java 8.0 on NonStop there really isn’t any
barrier to bringing every application to NonStop, something that has
become even easier when you consider the work HPE NonStop is doing with
their Yuma project to ensure a better mix and match of functionality
across system boundaries!
Would you like the application on Linux and the database on NonStop?
Would you like the transaction executing on NonStop and updating a
database on Windows? Very soon, or so it would seem, we will see
further boundaries crumble as we run NonStop as easily on a virtual
machine as we do on a real machine. IT will have forgotten all about
past issues of compatibility and transparency the more HPE mainstreams
NonStop.
In time NonStop will occupy a critical space amongst commercial,
off-the-shelf, servers, COTS, as they are called, it is an acronym
creeping into more of HPE’s presentations including those where “NonStop
as Software” participates. If you missed it, take a look at the material
being used to promote the first ever demonstrations given of NonStop
running in a virtual environment at the Mobile World Congress 2016 in
Barcelona, Spain, only a few weeks ago:
http://h71056.www7.hp.com/mwc/global/showcase
For the session HPE labelled, "Transfer to a hybrid infrastructure”
attendees were advised of a “demo to learn about the future of highly
available and massively scalable infrastructure for your core network.
This is a live demonstration featuring a potential HPE virtual NonStop
environment with x86 COTS hardware.” Like many within the NonStop
community we had heard from Martin Fink, EVP & HPE CTO, at last year’s
NonStop Technical Boot Camp that there had been a success in running
NonStop in this fashion within the labs. Transitioning to where live
demos could be performed is an altogether different story.
In presentations we have been giving for a number of months now, what
this all means is that, as we contemplate our own journey for DXOP to
where it will likely become the single code base we run on all open
platforms, including NonStop, our focus turns to providing more
functionality. We will begin shining the spotlight more brightly on DXOP.
Fault tolerance is important and as a community we should be placing
more emphasis on NonStop as the preeminent fault tolerant server. As IT
professionals we should also be more proactive in our exchanges with our
IT peers – and yes, as systems managers, we should be far more
expressive in all our communications with management.
NonStop systems may not be for everyone and NonStop systems may not
always be the right system for all applications. However when it comes
to transaction processing and the need to provide information in
customer facing situations, NonStop should be a first consideration - at
DataExpress we constantly remind our customers of the value it provides.
Shouldn’t everyone in the NonStop community be doing the same? And yes,
NonStop can teach much of the rest of IT about best practices, but watch
for more about that in a future article!
DataExpress, LLC.
1401 Shoal Creek, Suite 250, Highland Village, TX 75077
972-899-3476 (Sales)
972-899-3460 (Corporate)
sales@dataexpress.com
www.dataexpress.com
The OmniPayments 50%-Less Guarantee: How Do We Do That?
How does OmniPayments sell its popular NonStop-based financial transaction switch at a price that guarantees you 50% off your current transaction costs? Easy. It’s all in our pricing model.
Unlike other switch providers, who base your costs on transaction volume, OmniPayments sells you a one-time, perpetual software license. That is what makes the “50%-Less” difference. No volume fees. No transaction fees. No surprises. No penalties for company growth. All of our prices are presented to you up front. It’s just that simple.
In addition, our software leasing option allows you to acquire standalone OmniPayments with a minimal upfront investment.
Included within the OmniPayments License Fee are post-installation support services. The OmniPayments Service Level Agreement is very strong and is one of the reasons why financial institutions select us as their choice for a financial transaction switch.
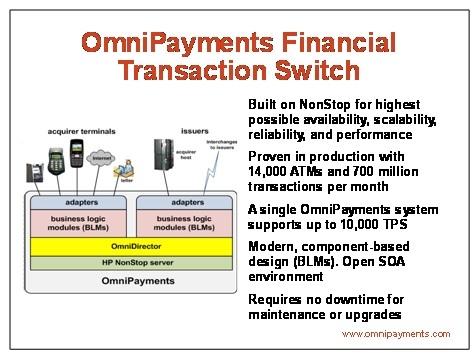
OmniPayments is a switching solution for the financial and retail industries. It is deployed on NonStop for the highest availability and offers all the requisite functionality to manage credit/debit-card transactions. It manages multiple devices, hosts application interfaces, and interoperates with third-party products or other systems if required. OmniPayments easily expands to provide additional functionality when needed and supplies complete security functions for every financial transaction handled, including encryption-at-rest and encryption-in-flight. Available around the clock, OmniPayments will survive any single fault, requires no downtime for maintenance or upgrades, and supports a range of disaster recovery solutions.
OmniPayments can be installed either as a complete, off-the-shelf solution or can be enhanced with customer-requested modifications and features to improve cost-effectiveness, efficiency, and risk mitigation. Our team of 100-plus NonStop specialists are skilled at rapid project turnarounds, meeting deadlines, and enhancing OmniPayments to address a customer’s specific requirements.
OmniPayments also distributes OmniCloudX on NonStop X. OmniCloudX hosts numerous OmniPayments instances at a pay-for-use price so attractive that mid-size retailers and financial organizations now can enjoy the benefits of having their own high-capacity transaction switches. Starts at only $5,000 USD per month. OmniCloudX is continuously available with automatic failover to other NonStop X systems. Like the OmniPayments standalone transaction switch, OmniCloudX provides complete security functions and is PCI-DSS compliant.
The OmniPayments Preauthorization Engine is used by financial institutions in conjunction with the OmniPayments Financial Transaction Switch or as a seamless interface to other providers’ switches via a custom support module (CSM).
A single OmniPayments system supports up to 10,000 transactions per second. Multiple OmniPayments systems can cooperate to provide any capacity required by an application. From our seven worldwide locations, we serve as a 24×7 managed services provider for remote production monitoring.
Visit the OmniPayments exhibit at GTUG on 18-20 April in Berlin, Germany. Along with our exhibit at BITUG’s BIG SIG in London on 12 May, OmniPayments CEO Yash Kapadia will present The OmniPayments Preauthorization Engine – Our Customers Call it the Fraud Blocker! Yash also will speak at N2TUG on 5 May in Plano, Texas (USA).
OmniPayments, Inc. (www.omnipayments.com) is the product arm of Opsol Integrators Inc., a leading HP NonStop system integrator. For further information, contact Yash Kapadia at +1 408-446-9274 or at yash@omnipayments.com.
XYPRO - HPE SecureData and XYGATE Data Protection™ (XDP), a powerful combination

HPE SecureData and XYGATE Data Protection™ (XDP), a powerful combination for tokenization on HPE Integrity NonStop Servers
When your customers and regulators are demanding protection and compliance but your application and infrastructure are resistant to change, something’s gotta give, right?
Not anymore. XYPRO knew that protecting data on the HPE NonStop server was going to be a serious challenge for anyone wishing to adopt powerful encryption and tokenization technologies, like HPE SecureData, to meet their customers’ and regulators’ demands.
Several years ago, XYPRO formed a partnership to work with Voltage Security, now known as
HPE Security – Data Security, the world leader in tokenization and format preserving encryption technologies, and developed XYGATE Data Protection™ (XDP) to simplify and optimize these solutions for the HPE NonStop marketplace and make them possible to deploy without any application changes or database modifications.HPE Data Security also knew that these technologies were an absolute necessity for security and compliance for their customers and acquired Voltage Security to form part of the HPE Enterprise Security Products division. HPE have also acquired the rights to deliver XYPRO’s XYGATE Data Protection™ (XDP) alongside HPE Data Security: SecureData to form this powerful combination.
To learn more about how HPE SecureData with XYGATE Data Protection™ (XDP) can help you address your security and compliance needs, read or download the latest datasheet from HPE on
Data Protection for HPE NonStop. XYPRO Technology Corporation
comForte - Demystifying Tokenization: Payment Versus Security Tokens
Payment
(high-value) versus security (low-value) tokens, and how both types of
tokenization can be part of an ideal payment security solution.
Mobile payments and electronic commerce (e-commerce) are booming
globally. Businesses continue to roll out innovative omnichannel
capabilities, which allow consumers to shop, purchase, and ship
merchandise from practically anywhere to basically everywhere. Indeed,
eMarketer
The growth has continued despite headlines revealing businesses’ ongoing struggles to protect payment data. In 2015, for instance, the U.S.-based Identity Theft Resource Center (ITRC) reported there were 781 total reported breaches, the second highest annual number on record since 2005 (when ITRC began tracking data). The 781 breaches exposed over 169 million records, which included 800,000 credit/debit card numbers.
Security concerns persist throughout the payment ecosystem, but solutions are emerging to address the threats and vulnerabilities that put primary account numbers (PANs) and other sensitive payment data at risk.
Read the full story and learn about the difference between payment and security tokens.
Gravic Publishes New HPE Shadowbase Case Study on
BASE24™ Business Continuity
Gravic recently published a new case study, Bank Chooses HPE Shadowbase Solutions for BASE24™ Business Continuity. A regional bank serving a major resort island took an aged BASE24 system and upgraded both the hardware platform and BASE24 software with no outages except for a brief disconnect/reconnect time during the final cutover. The bank also replaced a legacy costly data replication product with HPE Shadowbase software. In addition to bringing its system into PCI compliance, the bank implemented reliable failover procedures that reduced its downtime due to a production failure from two hours to under four minutes. The bank is now positioned to reduce its outage time to just seconds when it moves to a full Shadowbase sizzling-hot-takeover configuration. This case study illustrates that there are no barriers to choosing Shadowbase software as your BASE24 business continuity solution.
Gravic Presents on HPE Shadowbase Zero Downtime Migration (ZDM) Technology at March Events
At the March events of the SunTUG Sunshine Summit in Tampa, the MRTUG Meeting in Chicago, and the OTUG Meeting in Columbus, OH, attendees enjoyed our presentation, Reducing Downtime and Eliminating Risk for Disruptive Migrations with HPE Shadowbase Zero Downtime Migration (ZDM) Technology. This presentation demonstrated how customers are leveraging HPE Shadowbase solutions to perform zero downtime migrations for otherwise risky and disruptive application, database, and operating system upgrades. Several use case scenarios were reviewed for both homogeneous and heterogeneous migrations. Please contact us if you are interested in discussing this presentation’s content or having us present it to you or your colleagues.
To speak with us about your data replication and data integration needs, please visit us at www.ShadowbaseSoftware.com, email us at SBProductManagement@gravic.com, or call us at +1.610.647.6250.
Hewlett Packard Enterprise directly sells and supports Shadowbase Solutions under the name HPE Shadowbase. For more information, please contact your local HPE account team or visit our website.
Please Visit Gravic at these Upcoming 2016 Events
|
MENUG Events—Doha & Dubai, 12 &14 April |
|
|
|
GTUG IT Symposium—Berlin, 18-20 April |
|
|
|
BITUG BIG SIG—London, 12 May |
|
|
|
HPE NonStop Partner Tech Conference—Palo Alto, 24 May |
|
|
|
VNUG Conference—Stockholm, 12-14 September |
|
|
|
CTUG Conference—Toronto, 21 October |
|
|
|
Advanced NonStop TBC—San Jose Area, 13-16 November |
|
|
Please Visit Gravic at these Sites

CSP - New NonStop PCI Compliance and File Integrity Monitoring
Compliance Reporting Module (CRM) and File Integrity Checker (FIC) have rapidly become CSP's most acclaimed NonStop solutions and they are now being updated to provide even more protection.
Designed to meet the requirements of PCIDSS, Compliance Reporting Module (CRM) automatically performs hundreds of PCI related checks on NonStop servers to provide a "health report" with recommendations on how to fix any PCI compliance issues. In addition, users have free access to the CSP-Wiki which contains hundreds of recommendations on how to harden your Nonstop system against intrusions and attacks.
File Integrity Checker (FIC) monitors Guardian and OSS files for unauthorized modifications. FIC works by taking a unique file "fingerprint" of selected filesets and stores those fileset fingerprints in a secure database on the NonStop server. You can select multiple different filesets to be monitored, so that critical files can be checked frequently, and less critical files less often.
Both CRM compliance scans and FIC check runs can be scheduled in advance using the built in scheduler. FIC performs thorough checking of numerous file attributes automatically. These include:
· MD5/MD5-Incremental changes
· File Type modifications
· Last Modified timestamp
· File Status Changes
· File Owner changes
· Security Type (Safeguard or Non-Safeguard) change
· Safeguard Security Vector changes
· Guardian Security Mask changes
· Group Access
· Set UId
· Set GId
· EOF
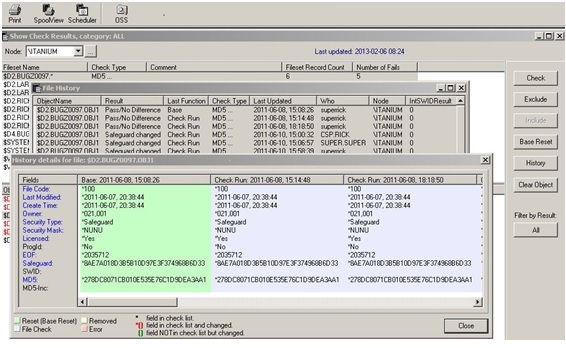
FIC stores its results in a database for historical comparison. With its MD5 Incremental checking capability, FIC can even monitor log files to detect if previously written records have been altered. With the included intuitive GUI interface, Both CRM and FIC have a full merged Audit capability and can also raise real time alarms for changes detected.
CRM Compliance and File Integrity from CSP. It's everything you could want for NonStop File Integrity and PCIDSS Compliance.
For more information on File Integrity Checker and our FREE NonStop Security Wiki, visit WWW.CSPsecurity.com.
CSP is a Platinum Sponsor at the upcoming GTUG HotSpot Event In Berlin, April 18 -20th, 2016. See you there!

We Built the Wiki for NonStop Security TM
Integrated Research
Sometimes you can be preemptive to the point where the coincidence may be hard to explain. Call it fortuitous and even accidental if you like, but the post to the IR blog of February 8, 2016, Can you Visualize NonStop in a Virtual World? has generated comments on multiple LinkedIn groups. They began appearing on the LinkedIn group, Real Time View , and then continued on the LinkedIn group, Connect HP User Group, following promotion of the IR post to these LinkedIn groups.
If you have not net joined in the discussion, you may want to follow the links above to see for yourself. I really would like to encourage you to do so, as this is all part of HPE NonStop development delivering on the goal of not just freeing NonStop from the hardware, but the infrastructure as well. The point is that as we get deeper into the topic of NonStop running on a virtual machine, there are as many opinions as there are members of the NonStop community. From where we stand here at IR, this is a huge sea change for NonStop, but one that we have been prepared to see occur for some time now – it’s almost as if the opportunity for future growth of NonStop needed it to embrace the way resources are provisioned these days just to remain relevant.
IR team members who have attended major HPE events of late report that there is renewed energy in support of the “mainstreaming of NonStop.” It is as if a corner has been turned and there is no going back. We recall clearly how it was NonStop that was funded to support the Intel x86 architecture, whereas there was no similar funding provided to do the same with HP-UX or even OpenVMS. It was NonStop too that benefited from the change to InfiniBand for the interconnect fabric to where, according to some recent statements, we can consider NonStop running on Commercial-Off-The-Shelf (COTS) hardware. And it was NonStop that is being freed from the hardware and became the “best software platform on the planet.”
This information has been well publicized since the curtain was lifted at the 2015 NonStop Technical Boot Camp, and then discussed again at the December 2015 HPE Discover event in London, as well as at the Mobile World Congress conference just held in Barcelona and reflected in the comments to both LinkedIn groups referenced above. But freed of the infrastructure is something altogether different from being simply free from the hardware as it elevates NonStop to being able to add value to most customers virtual environments that are becoming increasingly more commonplace as cloud computing makes its presence felt.
At IR we have been focused on telephony for many years and our Unified Communications (UC) offering has become a stalwart in the world of Voice over IP (VoIP). If you aren’t up to speed on this part of our product portfolio, you may want to check out the page, Take the headache out of multi-platform environments. Here you will read of how today we provide solutions to manage Avaya, Microsoft Lync and Cisco UC systems. Addressing multi-platform and multi-vendor environments is an area where IR has excelled and its significance shouldn’t be lost on the NonStop community.
As NonStop moves into environments where the infrastructure is of little concern, it will likely be part of a multi-platform and perhaps even multi-vendor environment. Furthermore, our experience with telephony, traditional telcos and mobile phone operators, has given us visibility into the world of virtualization – from our perspective, we have seen the broad adoption of a virtual world happening for some time. At one point, we thought NonStop would be vulnerable. But clearly, that is no longer the case.
What generated the comments to the LinkedIn groups following the post of February 8 was the news that NonStop would be publically demonstrated running in a virtual environment at the upcoming Mobile World Congress event. According to the promotion provided for the session Transfer to a hybrid infrastructure, “Visit this demo to learn about the future of highly available and massively scalable infrastructure for your core network. This is a live demonstration featuring a potential HPE virtual NonStop environment with x86 COTS hardware. Touch and see virtual network core functions of HPE I-HSS and INS."
Both products being showcased running on “a potential HPE virtual NonStop environment” were well known telco applications available from HPE for NonStop systems for some time. Even though the NonStop community had been informed that NonStop development had NonStop running in a virtual machine on Linux in their labs, the qualification at the time was that no, “It’s not ready to be a product, but it’s a proof point that we can get there.” Well, it is now clear that HPE NonStop has moved well past that point.
The timing of the February 8 post was not completely accidental, as it had been planned for several weeks, but it definitely proved to be fortuitous. Having said that, it is encouraging to see the NonStop community becoming as enthusiastic about the elevation of NonStop to where it is free from hardware and infrastructure (without losing its value proposition). The telco community may be the initial beneficiaries from running NonStop in a virtual world, but at IR we view this as just the beginning.
Anyone looking to begin the journey towards a hybrid infrastructure where the traditional IT systems are combined with private clouds, as HPE is so clearly predicting, will benefit from NonStop in a virtual world as well. The mainstreaming of NonStop we have all been hearing so much about of late is officially up and running!
Andre Cuenin
andre.cuenin@ir.com
3 REASONS TO CONSIDER LUSIS LITEPOS FOR 2016
Lusis LitePOS is a POS solution that allows organizations the ability to offer a secure, more cost effective, flexible and scalable POS environment to retailers. Independent of terminal suppliers, LitePOS combines traditional payments services with value-added services — such as gift cards, online loyalty, promotional offers and installment payments — to create a complete, tailor-made offering for retailers. As you’re planning for your organization and your merchants…
Here are 3 Reasons to Consider Lusis LitePOS for 2016:
REDUCE COSTS
Because of the lower costs associated with LitePOS, financial institutions can extend their POS terminal offerings to a wider base of smaller merchants. Allowing even those not currently using online or EMV-compliant POS devices to roll out these PIN-pad devices by providing them with access to secure payments services.
STANDARDIZE UPDATES
By deploying all of the logic and functionality within the LitePOS payments server, financial institutions can centralize all logic. Updates and changes can be implemented more quickly and standardized across a selected terminal estate.
IMPROVE SPEED-TO-MARKET
The SOA design of LitePOS, means changes to the solution can be made independently of each other. Testing and development time is significantly reduced, allowing organizations to quickly add value to payments for themselves and their merchants.
To learn more about how Lusis LitePOS can reduce your overall costs, make quicker standardized updates, and improve your speed-to-market, please contact me at: (630) 728-2734 or schedule a webcast at your earliest convenience.
BRIAN MILLER
VICE PRESIDENT AND GENERAL MANAGER, AMERICAS
Phone: 415-829-4577
Email: Brian.Miller@lusispayments.com
Website: www. lusispayments.com

Meet comForte at the European NonStop HotSpot event in Berlin
Stay connected and get the latest NonStop news at the European NonStop HotSpot event in Berlin, Germany, 18-20 April 2016!
The European NonStop HotSpot is your chance to take in keynotes from HPE, great presentations from HPE NonStop senior management and vendors, and an inspirational non-IT keynote speaker.
comForte has lots in store for you at the event including two new presentations, exciting product announcements, and the kick-off of the "comForte Challenge."
Meet up with NonStop colleagues both new and old, and learn the latest about NonStop from users, HPE, and vendors. And be sure to watch your email for more on what’s coming from comForte!
For an overview of the event and to register, visit the European NonStop HotSpot event page.
TANGO: THE "DO SOMETHING" OPTION TO LEGACY PAYMENT SYSTEMS
Is your legacy Payments platform getting too expensive to maintain? Is it unresponsive for today’s demanding and ever changing payment world? Has rapid transaction growth caused your 3rd party processing bill to reach the size of Fort Knox? Don’t know where to start to bring your payment processing in-house?
Too often, the fear and hassle of going through a conversion or platform migration leads to a "Do Nothing" strategy. In today's demanding and highly competitive world, to stay ahead of the competition one has to embark on a "Do Something" direction. Lusis Payments and our TANGO payments platform can help you DO SOMETHING!
Whether you decide for a big-bang conversion, or a phased approach of feathering in new technology to gradually replace your legacy environment, NOW is the time to start planning.
If you're ready to “DO SOMETHING” visit our website, download our new solution paper on Legacy Payment Systems or schedule a webcast on the TANGO solution.
BRIAN MILLER
VICE PRESIDENT AND GENERAL MANAGER, AMERICAS
Phone: 415-829-4577
Email: Brian.Miller@lusispayments.com
Website: www. lusispayments.com

Spring Events Summary

NuWave Technologies has been busy attending many of the events around the country this spring, and are gearing up to attend some in Europe in the coming months.
See what NuWave thought of
If you are in Europe, don't miss your chance to connect with NuWave at these amazing events to learn more about how you can modernize your NonStop systems easily and cost effectively.
GTUG: April 18-20
BITUG: May 12
Learn more about these events on NuWave's website.
Interested in connecting with NuWave at these upcoming events? Email David Ross (davidross@nuwavetech.com) to schedule a time to meet.
The Availability Digest Reviews the HPE Cyber Risk Report 2016
HPE recently released its extensive (96 pages) 2016 Cyber Risk Report.
It examines the vulnerabilities that expose organizations to data
breaches. The report provides insights into how security funds and
personnel can be allocated better to counter cyber threats and to
prepare proper breach responses. Prepared and distributed by the HPE
Security Research Team, the report focuses on seven key themes. Among
them are: overreaching regulations push research underground, the
monetization of malware, and the industry didn’t learn anything about
patching in 2015.
In addition to “HPE Cyber Risk Report 2016,” read the following articles
in the Availability Digest’s March 2016 issue:
Australia’s Telstra Downed by Fat Finger –Telecommunications company
Telstra connects its customers to the Telstra network via ten connection
points called nodes. They provide tremendous redundancy. Around Noon on
9 February, a malfunctioning node was taken down for maintenance by a
Telstra engineer who unfortunately did not follow rerouting procedures.
Instead of moving customers to a functioning node, the engineer
reconnected them to the downed node. Suddenly 10% of Telstra’s customers
– about 1.5 million businesses and individuals – found themselves
without mobile or landline telephone services. Internet connections were
impacted as well.
How the Ukraine Power Grid Was Hacked – The Digest and other
publications have donated much print space to the 23 December 2015
breach of Ukraine’s power grid, believed to be the first-ever incident
of hackers causing a widespread power outage. After months of forensic
analysis, Ukraine is releasing details about how the attack was carried
out. It all began with a phishing campaign.
High-Voltage Transformers – The Power Grid’s Achilles Heel – The U.S.
power grid is famously reliable in that seldom do outages last weeks or
even days. However, a significant vulnerability to the power grid is the
risk of destruction of an extra-high-voltage (EHV) transformer.
Monstrous in size, a challenge to transport, and prohibitively
expensive, a damaged EHV can take months or more to repair or replace.
Enter the RecX transformer. Smaller than EHVs, easily transportable, and
economical to produce, the RecX is the key component to the U.S. rapid
replacement strategy.
@availabilitydig – The Twitter Feed of Outages - Our article highlights
some of our numerous tweets that were favorited and retweeted in recent
days.
The Availability Digest offers one-day and multi-day seminars on High
Availability: Concepts and Practices. Seminars are given both onsite and
online and are tailored to an organization’s specific needs. We also
offer technical and marketing writing services as well as consulting
services.
Published monthly, the Digest is free and lives at
www.availabilitydigest.com. Please visit our Continuous Availability
Forum on LinkedIn. We’re at 743 members and counting. Follow us as well
on Twitter @availabilitydig.
comForte at events near you in 2016
|
MENUG |
11 Apr 2016 |
Riyadh, RSA |
|
MENUG |
12 Apr 2016 |
Doha, Qatar |
|
MENUG |
14 Apr 2016 |
Dubai, UAE |
|
International GTUG |
18-20 Apr 2016 |
Berlin, Germany |
|
VNUG |
12-14 Sept 2016 |
Stockholm, Sweden |
|
PCI DSS US |
20-22 Sept 2016 |
Las Vegas, USA |
|
PKF |
3-4 Oct 2016 |
London, UK |
|
PCI DSS EU |
18-20 Oct 2016 |
Edinburgh, Scotland |
|
CTUG |
21 Oct 2016 |
Canada |
|
NonStop TBC |
13-16 Nov 2016 |
San Jose, USA |
Please contact us if you would like to arrange meetings with our team at any of these events.
XYPRO looks forward
to seeing you throughout 2016
PCI SSC Middle East Forum April 6, 2016 - April 7, 2016 Dubai, U.A.E
MENUG – Riyadh, RSA April 11, 2016 Saudi Arabia
MENUG – Doha April 12, 2016 Doha, Qatar
MENUG – Dubai April 14, 2016 Dubai, UAE
European NonStop HotSpot April 18, 2016 - April 19, 2016 Berlin, Germany
BITUG BIG SIG May 12, 2016 London, UK
ACI User Group Exchange June 6, 2016 - June 9, 2016 Orlando, Florida
VNUG September 12, 2016 - September 14, 2016 Stockholm, Sweden
PCI North America 2016 September 21, 2016 - January 22, 2016 Las, Vegas, NV
PCI Europe 2016 October 19, 2016 - October 20, 2016 Edinburgh, Scotland
CTUG 2016 October 21, 2016 Mississauga, Ontario, Canada
PCI Asia Pacific 2016 November 16, 2016 - November 17, 2016 Singapore
Find out more about us at
www.tandemworld.net
+44 (0) 20 8304 7979
We would like to thank the sponsors of the March 2016 eNewsletter
Platinum Sponsor
Gold Sponsor
Silver Sponsor
To enquire about Sponsorship opportunities for the Tandemworld Newsletter please click here.
Current Subscribers 15102
Our company, Tandemworld, accepts no
liability for the content of this email, or for the consequences of any
actions taken on the basis of the information provided.
To Unsubscribe or Change your Subscription Please click here


